Computer Scientists Call for Recount of 2024 Election
Jessica Denson discuses the irregularities of the 2024 election.
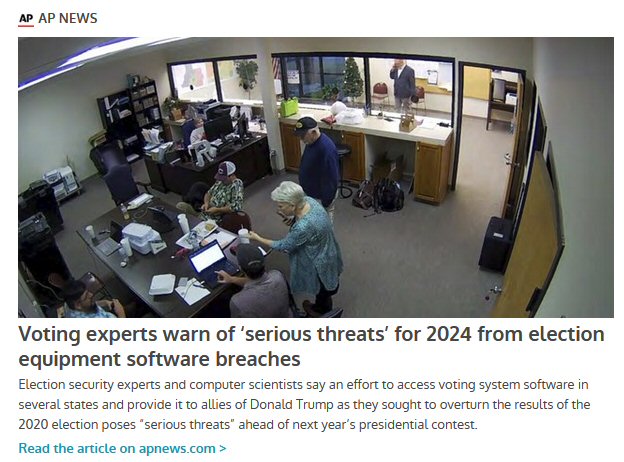
Per the above article: An effort to access voting system software in several states and provide it to allies of former President Donald Trump as they sought to overturn the results of the 2020 election has raised “serious threats” ahead of next year’s presidential contest, according to a group of experts who urged federal agencies to investigate.
The letter sent by nearly two dozen computer scientists, election security experts and voter advocacy organizations asks for a federal probe and a risk assessment of voting machines used throughout the country, saying the software breaches have “urgent implications for the 2024 election and beyond.” The breaches affected voting equipment made by two companies that together count over 70% of the votes cast across the country, according to the letter.
“The multistate effort to unlawfully obtain copies of voting system software poses serious threats to election security and national security and constitutes a potential criminal conspiracy of enormous consequences,” the group wrote in a letter sent to U.S. Attorney General Merrick Garland, special counsel Jack Smith, FBI Director Christopher Wray and Jen Easterly, director of the U.S. Cybersecurity and Infrastructure Security Agency. “We must protect our most sacred tenet of democracy — the security of our vote.”
The full extent of who received the bomb threats is not clear. None are believed to have been deemed credible. NBC News compiled a list of 67 locations in 19 counties, based on local news reports and state and local election officials’ statements, all of which appear to have received similar threats. Of the 67 locations, 56 were in 11 counties that voted for Joe Biden in the 2020 election, including the eight most populated. Those high-population Democratic counties include voting locations for Milwaukee, Wisconsin; Detroit, Michigan; Phoenix, Arizona; Atlanta, Georgia; and Philadelphia, Pennsylvania.
Maricopa County, Arizona, which Biden won by a slim margin, has consistently been the subject of election denialism conspiracy theories. The other five — Michigan’s Wayne County, Pennsylvania’s Philadelphia County and Georgia’s DeKalb, Fulton and Gwinnett counties — were some of the largest Democratic strongholds in their respective states.
Computer Scientists: Breaches of Voting System Software Warrant Recounts to Ensure Election Verification – Free Speech For People
A group of computer security experts have written to Vice President Kamala Harris to alert her to the fact that voting systems were breached by Trump allies in 2021 and 2022 and to urge her to seek recounts in key states to ensure election verification.
Per the above article: “A group of computer security experts have written to Vice President Kamala Harris to alert her to the fact that voting systems were breached by Trump allies in 2021 and 2022 and to urge her to seek recounts in key states to ensure election verification. Vice President Harris argues that this extraordinary and unprecedented breach in election system security merits conducting recounts of paper ballots in order to confirm computer-generated tallies. The letter also highlights the fact that the post-election audits in many key states will be conducted after certification and after the window to seek recounts closes, and that therefore recounts should be sought promptly.
The letter states: “Possessing copies of the voting system software enables bad actors to install it on electronic devices and to create their own working replicas of the voting systems, probe them, and develop exploits. Skilled adversaries can decompile the software to get a version of the source code, study it for vulnerabilities, and could even develop malware designed to be installed with minimal physical access to the voting equipment by unskilled accomplices to manipulate the vote counts. Attacks could also be launched by compromising the vendors responsible for programming systems before elections, enabling large-scale distribution of malware.”
“In December 2022 and again in 2023, many of us, concerned by the security risks posed by these breaches, wrote to the Attorney General, FBI Director, and Cybersecurity and Infrastructure Security Agency (CISA) Director outlining the security concerns and urging an investigation. Though there have been limited, localized investigations, there is no evidence of a federal investigation to determine what was done with the misappropriated voting software.”
The letter is signed by Professor Duncan Buell, Ph.D., Chair Emeritus — NCR Chair in Computer Science and Engineering, Dept. of Computer Science and Engineering, University of South Carolina*; David Jefferson Ph.D., Lawrence Livermore National Laboratory* (retired), Election Integrity Foundation*; Susan Greenhalgh, Senior Advisor for Election Security, Free Speech For People; Chris Klaus, Chief Executive Officer, Fusen World*; William John Malik, Malik Consulting, LLC*; Peter G. Neumann Ph.D., Chief Scientist, SRI International Computer Science Lab*; and Professor John E. Savage, Ph.D, An Wang Professor Emeritus of Computer Science, Brown University*.
TEXT OF LETTER SENT TO VICE PRESIDENT HARRIS BY COMPUTER SCIENTISTS
November 13, 2024
The Honorable Kamala Harris
The White House Office of the Vice President
1600 Pennsylvania Avenue, N.W.
Washington, DC 20500
Dear Vice President Harris,
We write to alert you to serious election security breaches that have threatened the security and integrity of the 2024 elections, and to identify ways to ensure that the will of the voters is reflected and that voters should have confidence in the result. The most effective manner of doing so is through targeted recounts requested by the candidate. In the light of the breaches we ask that you formally request hand recounts in at least the states of Michigan, Nevada, Wisconsin, and Pennsylvania. We have no evidence that the outcomes of the elections in those states were actually compromised as a result of the security breaches, and we are not suggesting that they were. But binding risk-limiting audits (RLAs) or hand recounts should be routine for all elections, especially when the stakes are high and the results are close. We believe that, under the current circumstances when massive software breaches are known and documented, recounts are necessary and appropriate to remove all potential doubt and to set an example for security best practices in all elections.
In 2022, records, video camera footage, and deposition testimony produced in a civil case in Georgia1 disclosed that its voting system, used statewide, had been breached over multiple days by operatives hired by attorneys for Donald Trump. The evidence showed that the operatives made copies of the software that runs all of the equipment in Georgia, and certain other states, and shared it with other Trump allies and operatives.
Subsequent court filings and public records requests revealed that the breaches in Georgia were part of a larger effort to take copies of voting system software from systems in Michigan,5 Pennsylvania,6 Colorado7 and Arizona,8 and to share the software in the operatives’ network. According to testimony and declarations by some of the technicians who have obtained copies of the software, they have had access for more than three years to the software for the central servers, tabulators, and highly restricted election databases of both Election Systems & Software (ES&S), and Dominion Voting Systems, the two largest voting system vendors, constituting the most severe election security breach publicly known.
Combined, their equipment counts nearly 70% of all votes nationwide. Ninety-six percent of Arizona voters use Dominion and ES&S equipment; 100% of Georgia voters vote on Dominion machines; 98% of Nevada votes on Dominion voting machines and the remainder uses ES&S; 69% of Michigan voters’ ballots are counted on Dominion or ES&S equipment; 89% of Pennsylvania voters ballots are counted on Dominion or ES&S equipment; ES&S counts 92% of North Carolina ballots; and either ES&S or Dominion counts 97% of Wisconsin votes.
Possessing copies of the voting system software enables bad actors to install it on electronic devices and to create their own working replicas of the voting systems, probe them, and develop exploits. Skilled adversaries can decompile the software to get a version of the source code, study it for vulnerabilities, and could even develop malware designed to be installed with minimal physical access to the voting equipment by unskilled accomplices to manipulate the vote counts. Attacks could also be launched by compromising the vendors responsible for programming systems before elections, enabling large scale distribution of malware.
In December 202212 and again in 2023,13 many of us, concerned by the security risks posed by these breaches, wrote to the Attorney General, FBI Director, and Cybersecurity and Infrastructure Security Agency (CISA) Director outlining the security concerns and urging an investigation. Though there have been limited, localized investigations,14 there is no evidence of a federal investigation15 to determine what was done with the misappropriated voting software.
Other relevant parties have pointed to the serious risks posed by the misappropriation of the voting software. Before it was known that partisan operatives had taken the software, Dominion Voting Systems objected vehemently to providing its software to the same partisan actors who ultimately got copies through voting system breaches, stating that to give its software to biased actors would cause “irreparable damage” to the “election security interests of the country.”
Before the breaches in Georgia had been confirmed, the Georgia Secretary of State’s chief information officer testified that having copies of the software would provide a “road map” to the ways the system could be accessed. The Georgia Attorney General opposed providing copies of the software to lawyers for the Trump campaign in a late 2020 election challenge, arguing that images of the voting system software would provide “the keys to the software kingdom.”
Notably, U.S. elections are potentially resilient because there are paper ballots recording the voters’ intent in most states, meaning that even if the voting system is at risk, the will of the voters can be determined reliably by recounting the paper ballots by hand (although we are aware that not all paper ballots are verified by the voter, and not all states take adequate care to protect the ballot chain of custody.)
Audits will be conducted in some of the most scrutinized states, but in key states they will not be conducted in a timely way that could reveal any concerns with the vote count. In addition, in most states the audits are insufficiently rigorous to ensure any potential errors in tabulation will be caught and corrected, and they cannot be considered a safeguard against the security breaches that have occurred. Specifically, Georgia’s audits are non-binding, and Michigan, Nevada and Wisconsin laws do not provide that the audit be conducted before certification. Therefore, it would be impossible to know for these critical states if the audits uncovered errors or miscalculations before the state deadlines to seek recounts.
Among swing states, only Arizona’s audit laws ensure that, if enough discrepancies are identified, the audit hand count will be expanded to correct a potentially incorrect result. In other words, aside from Arizona, in contested states, there is no legal mechanism for the audit to correct the outcome, no matter how much error the audit uncovers. Given these facts, the only guarantee for rigorous, effective audits of the vote in the swing states will be through candidate-requested statewide hand recounts.
The facts around the voting system breaches are not disputed; it is well-documented that there were severe, multiple voting security breaches before the 2024 election. To ensure that voters can have confidence that the breaches in security did not taint the results of the 2024 election, we recommend pursuing hand recounts in, at minimum, Michigan, Nevada, Wisconsin and Pennsylvania as they will provide insufficient safeguards against threats posed by the breaches of the election software and will not provide important information in a timely way.
Thank you for your time and consideration of this important matter.
Sincerely,
Duncan Buell Ph.D.
Chair Emeritus — NCR Chair in Computer Science and Engineering
Dept. of Computer Science and Engineering
University of South Carolina*
David Jefferson Ph.D.
Lawrence Livermore National Laboratory* (retired)
Election Integrity Foundation*
Chris Klaus
Founder
Internet Security System*
Susan Greenhalgh
Senior Advisor for Election Security
Free Speech For People
William John Malik
Malik Consulting, LLC*
Marilyn Marks
Executive Director
Coalition for Good Governance
Peter G. Neumann Ph.D.
Chief Scientist,
SRI International Computer Science Lab*
John E. Savage
An Wang Professor Emeritus of Computer Science
Brown University*
https://www.youtube.com/live/
Jessica Denson speaks with Duncan Buell PhD, Chair Emeritus of Computer Science and Engineering at the University of South Carolina, who penned a letter with other top election security experts to the White House alerting VP Harris that she should request recounts in swing states.
Cyber Security Expert Stephen Spoonamore’s Letter to Kamala Harris about the 2024 Election
November 15, 2024
Honorable VP Kamala Harris
The White House
Office of the Vice President
1600 Pennsylvania Ave
Washington DC 20500
Dear Madam Vice President.
This is my second Duty to Warn Letter regarding hacking of the 2024 Presidential Election. The first letter on November 7 was directed to Commonwealth of Pennsylvania Officials. Both warnings are made per DNI Clapper’s 2015 directive to all agencies and contractors associated with intelligence and financial agency technologies to warn of suspicions of hacking.
Professionally I have worked as the CEO or CTO at seven high technology firms including two which specialized in hacking and counter-hacking operations. My clients have included numerous governments DoD, DHS, Dept. of State, F100 Financials and F500 Industrials.
I am a lifelong Republican who has long placed service and participatory democracy over party. In government, I have twice been invited to SoCom to give lectures on electronic warfare and techniques to find terrorist money laundering and gave a keynote speech of the National Counterintel Summit on this same topic. I served as an after-action reviewer of communications and data failures on 9/11 under the direction of Jim Woolsey and FDNY Commissioner Scopetta, and later co-wrote multiple hacking risk analysis of Smart Grid technologies for the Obama administration.
You should reverse your concession, call for both a full investigation of criminal activity and demand hand recounts in all seven swing states.
In my professional view there are multiple and extremely clear indications the Presidential vote was willfully compromised.
I wholly agree with the public letter of Duncan Buell, et. al. of Nov. 13th stating they believe there is a possibility of hacking and calling for hand-recounts.
This letter’s clear call to action is commendable, but its cautious tone may belie the severity of what I believe has happened. In my view it is a near certainty the results have been changed at a scale which reversed the US Presidential Election. They imply there is a chance a hand-recount will show you won more votes. I am stating a hand recount will most likely show you did win. Both letters call on you to act.
In my view, a capable and skilled series of exploits, electronic tools and hacks were used to change the Presidential vote in all seven swing states. These activities have reversed the outcomes in at least Arizona, Michigan, North Carolina, and Wisconsin. I will lay out the basics of the attack, starting with unusual elements within the results. I will then outline two processes which could have been followed to insert these false results into the system. Finally I will outline how I would recommend investigating.
Unusual elements within the results.
The results of the attack are improbable in the extreme and well tailored to the sole benefit of your opponent.
Approximately 600,000 votes are for Donald Trump but with no down ballot choices. These are either inserted “bullet ballots” for the Presidential race or manipulated data fields. They are surgically added to totals in limited jurisdictions and within only the seven swing States. This historically unprecedented set of numbers found in the 2024 swing states is absent in every other state. In AZ, MI, NC and WI the effect of these drop-off votes reverses the voters’ will and even more improbably always pushes the winning margin beyond the mandatory recount numbers.
It is a result too perfect for belief. It is a bespoke and programmed outcome. In other states including PA and NV, removing these strange and bespoke added votes, it appears Donald Trump may have won the cast votes but within a margin which would force recounts. The inserted votes raise his totals, to avoid any scrutiny during mandatory recount results which would have slowed his claim on the Presidency. In GA and FL the same pattern exists with unclear impact on the results.
This attack is not technically difficult. It is modest in scale. It would require:
Modest and common computer programming skills.
Access to 10-100 tabulators or to the handful of facilities programming them in advance.
A credible database of voter IDs of non-voters around which to create false ballots.
Perhaps as few as 1, but more likely 3-5 human program managers.
Access to eBollBook Data during the election to determine who had not voted.
(Possibly) Human access to some tabulators during counting.
If I was asked to lead this hack, I would expect to have a core team of 6-10 people, and operating costs under $10M with a timeline of 3-12 months.
The tell: A historically absurd number of Trump-only bullet ballots or undervote ballots.
There are always a handful of voters who cast a vote in one race which they care about, and do not make other selections on the ballot. These are called bullet ballots. In Presidential Races since 1980, these bullet ballots rarely account for more than 1% of the total votes including in Mr. Trump’s winning 2016 election and losing 2020 election, and when they do it warrants further investigation. In 2024 in the 43 non-swing states, bullet ballots make up a nominal >1%. In the seven swing states the numbers are so high to be unbelievable, unprecedented and demanding of further investigation. Here is analysis from totals as of late Nov. 12th
Here are the unprecedented results of drop-offs in the two western swing states:
AZ – 123K+ 7.2%+ of Trump’s total vote. Enough to reverse the outcome.
NV – 43K+ 5.5%+ of Trump’s total vote. Enough to exceed recount threshold.
It is my belief these two states have illegally added votes.
For comparison, examine Trump’s 2024 results in three states which border AZ and NV. They have equally passionate Trump supporters, but have the normal levels of drop off or bullet ballots.
ID <2K 0.03% of Trump’s total.
OR <4K 0.05% of Trump’s total
UT <1K 0.01% of Trump’s total.
In the case of Idaho and Utah, Mr. Trump was a run-away winner and had no need to add votes. In the case of Oregon, Ms. Harris was a run-away winner and adding votes to Trump’s total would add risk without adding value.
The same pattern of large numbers of drop-off votes or bullet ballots exists in the totals of MI, NC, PA, WI.
North Carolina is the most extreme. The public results indicate over 350K voters cast a ballot for Trump and no other race making up over 11% of Trump’s voters in NC drop off votes or bullet ballots.
Hack Part 1: Creating the pool of bullet ballot voters.
There are two possible methods to execute this attack. The simple version would only manipulate electronic totals and hand-counting the target precincts would discover this. The second involved ePollbook hacking and introducing bullet ballots. This would add the need to compare the ePollBook timestamps to find possible bad actors or other sources for these anomalous votes.
When Mr. Musk announced his $1M lottery for people to go online and sign a pledge to vote for Trump, I became personally suspicious of why such a promotion would be done. I signed up to see what information he wanted and what the pledge actually stated. He did not want to know people’s socials or send them texts. To sign up you had to provide your street address. That was all they cared about. Once they had the people’s names, and street address this would allow for building a pool of ghost voters who could logically be marked for fake ballots, structured in a manner which matched ePollBook and precinct data. You, as a member of law enforcement, understand criminals need certain pre-conditions to act. A database of pledged supporters with street addresses is required for this hack. Law enforcement should immediately find the team of programmers who pulled the lottery data capture. They will find those programmers immediately parsed the data into a system based on voting precincts and created macros to constantly update the pledged lists of who had cast a vote, and who had not. The programmers likely did not know they were working on a system to be used to steal the election. When confronted with that fact, law enforcement would likely gain cooperating witnesses.
Musk’s team used this system to build a list of voters pledged to vote for Trump. This list could also be used to make a ghost-ballot voter list. ePollBook data is nearly always linked to the internet, and in many jurisdictions this link was being made in real time via Mr. Musk’s Starlink or any available wireless network. Throughout the day, Musk’s team could compare existing turnout models to likely outcomes, based on well established voter profile databases vs. the actual voter turnout coming in from the ePollBooks. They would have been able to have a very good estimation in the closing hours of polls how many votes short Trump would likely be at the tabulation level. They would also have exact lists of the pledged voters for Trump and would know who had not shown up. The pledged voters who did not vote, became the bullet ballots. With any network connection to the ePollBooks, or via other compromised connectivity, they could be marked as voted.
Hack Part 2: Matching the tabulation to the ePollBooks.
The exact number of added voters to the ePollBooks as having voted would have to match the tabulation process. This attack could have been done in at least two different ways.
The easiest method to execute phase two, is also the easiest to discover by hand-recount. In a few jurisdictions where the tabulators either had network connectivity, approved or otherwise, or where a person on the team had physical access to the tabulation machine, the Trump votes that were added to the ePollBooks, would need to be added to the tabulators. At which point the ePollBooks and the tabulation totals would match, having been digitally stuffed with demographically credible voters for Trump. But there will be no paper ballot for these votes. A hand-recount will quickly discover the fraud.
As I write this letter, several hundred people are self organizing on Reddit and other forums. They include: data scientists, statisticians, and legal experts. They are examining the precinct level data of every swing state, and by Monday these teams will have lists of many precincts where these historically unprecedented Trump bullet ballots occur. The highest likelihood is that those ballots don’t actually exist. Those votes were electronically created but have no paper. This would be easily proven with a hand recount.
A second possibility involves the same compromise as described above, but is then combined with human ballot stuffing, or ballot substitution, at tabulation to match the epollbook numbers. This possibility is raised as it appears these historically unprecedented bullet ballots fall heavily in a few counties. Maricopa County AZ, seems to be the source of the vast majority, perhaps nearly all, of the AZ bullet ballot voters for Trump. If these ballots were introduced it would require co-conspirators working inside the tabulation center.
I appreciate that many people, even sophisticated people outside this field, think this hack is an impossible task. It is not. Just 8 weeks ago the world watched a vastly larger and more complicated one. Unknown hackers intercepted over 3000 communications devices over 24 months destined for use by Hamas across the entire Mideast. The devices all had additional software, hardware and explosives inserted. The devices were then delivered to users and functioned normally for months until the hackers triggered the inserted series of exploits and explosions.
This hack, the entire world witnessed, was orders of magnitude more complicated than introducing Trump bullet ballots into – at most – 100 tabulation locations. I have personally managed full year long operations in which hundreds of credit card point of sale devices were rebuilt with added hardware and software and inserted in order to discover fraudsters and money laundering. No one knew we were there. The users never were aware. The devices did their normal job processing credit cards for merchants. While they also did a hacked job and helped my team and I root out criminals. The access, technical difficulty, and scale of the election hack I am describing is less than either of these. But the effect is vastly greater, and the FBI has excellent people who could address this very quickly.
Lastly, this hack methodology may or may not have some correlation with the series of Bomb Threats called in by Russian affiliated assets. The use of distraction or diversion of this kind is common. My first thought was, and my thinking remains, these bomb threats were called into tabulation centers and precincts where the hackers had already planned to conduct ghost bullet ballot introductions. I believe they wanted a disruption in the chain of custody, so lawyers could claim after the hacking events that the chain of custody on the ballots was flawed. The creation of the false-argument of a broken custody chain would be used as a pretext to prevent hand recounting, as hand recounting would not match the Trump favorable result. However, by a reverse of that logic, any jurisdiction which was subject to a bomb threat was forced to break standard operating procedure. This alone should be grounds for you to ask for a hand-recount.
Lastly, I have been advised by an attorney that Arizona and Georgia have mechanisms in place for members of the public to demand a recount, but only you have the ability to demand a recount across all the jurisdictions of concern.
A final formal note. This is principally a Duty to Warn letter. It is also a fulfillment of my constitutional oath of office as possibly the lowest level sworn office of public trust in America. I was appointed by my township to serve as a local Parks Commissioner. I am the public appointee to the Mt. Nittany Conservancy, a nature reserve. I have spent the last four years variously overseeing how public funds are spent on sports fields, kids playgrounds, hiking trails, and bike paths. To do this, I must make annual conflict and financial disclosures and I must swear nearly the same oath you did. I am under the sworn obligation to defend our nation against all enemies, foreign and domestic. Which, I am honored to do.
I will continue to investigate with a growing group of volunteers. We are also planning to offer rewards for information. But our efforts to preserve the integrity of this election can not take this to completion. You, and only you, can call for a full hand-recount and engage the vast public resources at your disposal. I can’t. This is all I can do.
Let me know how I can help.
Sincerely,
ESignature – Stephen R. Spoonamore
College Township PA
Former CEO or CTO of multiple Technology Firms
https://www.linkedin.com/in/spoonamore/
CC: Secretary. of States and Governors of AZ, FL, GA, MI, NC, NV, PA and WI. Additional PA representative Chris Dush (PA State Sen.), Paul Takac (PA State Rep.), Dustin Best (PA College Township Supervisor), and Robert Ziegler (PA Milhiem Township Supervisor.)
COPY OF LETTER TO PA GOVERNOR JOSH SHAPIRO FROM CYBER SECURITY EXPERT STEPHEN SPOOMAMORE ABOUT THE 2024 ELECTION

Stephen Spoonamore, the data scientist behind a viral “duty to warn” has uncovered results from an analysis of the 2024 election, specifically an inconsistency in bullet ballots
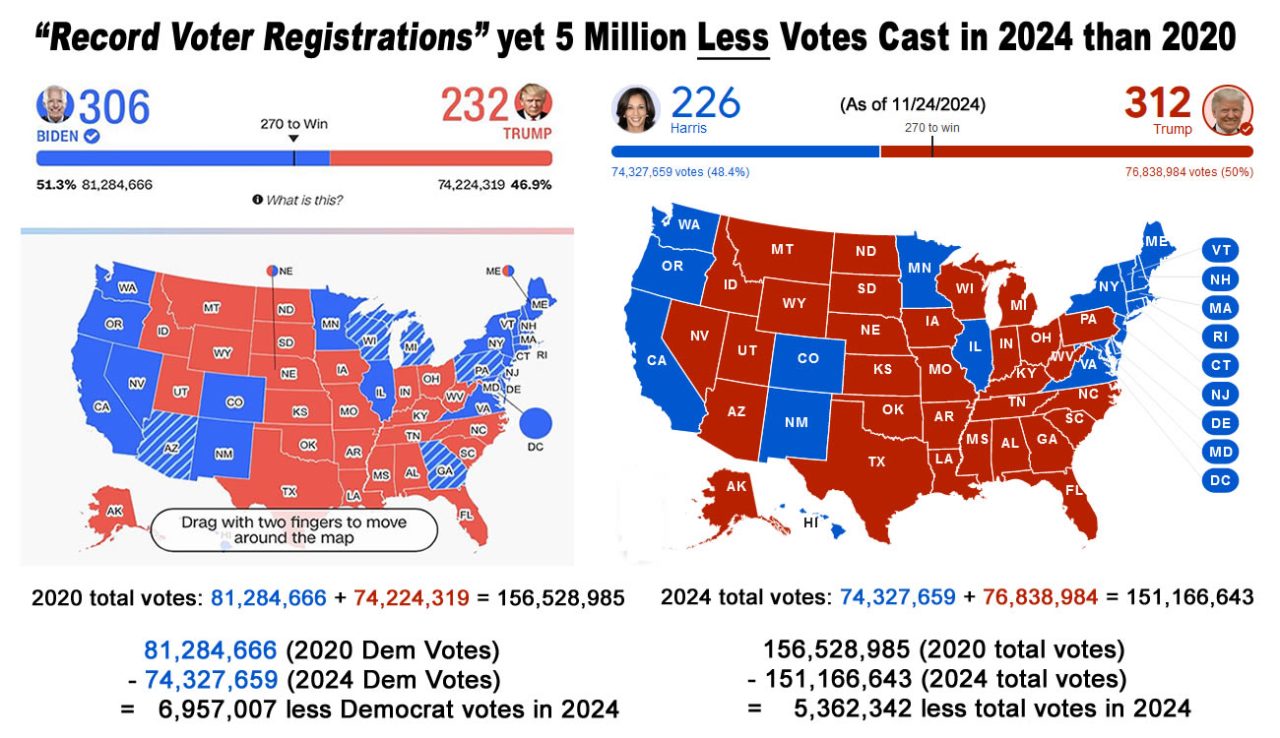
As motivated as Americans were about this being the most important election in the history of the United States… reports of ‘Record New Voter Registrations’, including 337,000 attributed to Taylor Swift, stadiums full of supporters at rallies never seen by Joe Biden, Republican voters crossing over to vote for Kamala, a record number of women voting for Abortion Rights, Trump saying he was going to be a ‘Dictator on day one’, saying he was going to lock up opponents who criticized him, saying news outlets which criticized him should be shut down, saying people who criticized the Supreme Court should be jailed, a pathological liar who lied over 30,000 times while president, an adjudicated rapist & convicted criminal with 88 criminal charges, his outrageous, hateful, insane conduct, his inciting an insurrection which caused 5 deaths and injuries of countless Capitol Police, it defies logic that more people voted for Trump than Harris. It also defies logic that according to the official vote count, less people voted in 2024 than 2020.
To believe that Trump legitimately won the 2024 election you must believe that the majority of Americans are stupid & do not care about Trump’s outrageous behavior and have no decency or principles. You must also believe that the majority of Americans doesn’t care about Democracy, Freedom of Speech or Freedom of the Press, because Trump has promised to be a ‘Dictator on Day One’ and eliminate all descent.
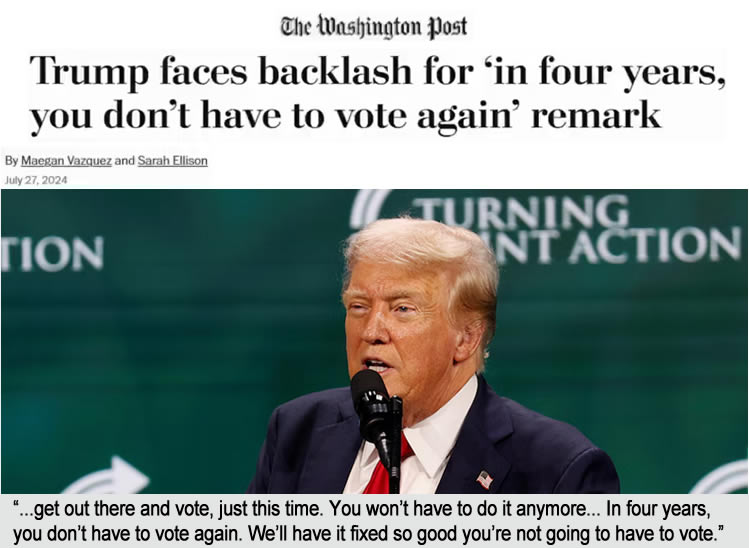
Trump admitted the 2024 election and future elections will be rigged when he said “I don’t need your votes”. “Get out and vote just this time…. you won’t have to do it anymore… we’ll have it fixed so good, in four years you don’t have to vote again”.

Kamala Harris kept saying during the 2024 election ‘When we Fight, We Win’. She is now proving those words to be a empty campaign slogan and has proved she is a COWARD by failing to demand recounts in Swing States.
VP Harris has IGNORED letters from Cyber Security Experts dated 10/13/2024 & 10/15/2024 urging her to recount the votes in Swing States as detailed on this site. Harris BETRAYED everyone who voted for her by failing to demand recounts by November 27, which was the last day to request recounts for all swing states. Although outside organizations can order recounts, election experts say it is now TOO LATE to reverse the 2024 election even if they find proof the election was rigged. It is still vital that recounts be conducted to established if the election was rigged and determine if Trump is a illegitimate President who stole the election as millions of Americans believe and therefore has no ‘mandate’ by the majority of voters.
If recounts by independent organizations show the 2024 election was hacked & stolen, and Trump is found to be an illegitimate President Elect, VP Harris, Democrats and the Media will be as culpable as Republicans for helping to put Trump in the White House.
Trump is a lying, lawless, wannabe Dictator Lunatic who Mental Health professionals have called “a paranoid, , narcissist, psychopathic Frankenstein monster who is divorced from reality”, as shown in the above video.
In 4 years, elections in the U.S. could be like Orban’s Hungary and Putin’s Russia… merely ‘window dressing’ where elections will be rigged for Republicans, who have been subverting Democracy for years by Gerrymandering, Voter Purges and other unscrupulous tactics.
Call the DNC, the White House, Kamala Harris, Tim Waltz and Democrat congressmen and demand a recount